题目名称 吾的字节
啊,吾的字节!呃~我为什么要说吾?

题目附件给了一个二维码,可以看见里面有小像素点
扫描结果:flag is no here, see the QRcode clearly!看来要提取一下了
用ps经行查看可以知道每个像素点为等间距用脚本提取一下
from PIL import Image
img = Image.open("five.png").convert("L")
threshold = 128
with open("output.txt", "w") as f:
for y in range(5, 296, 10):
row_bits = ""
for x in range(5, 296, 10):
pixel = img.getpixel((x, y))
bit = "1" if pixel < threshold else "0"
row_bits += bit
f.write(row_bits)
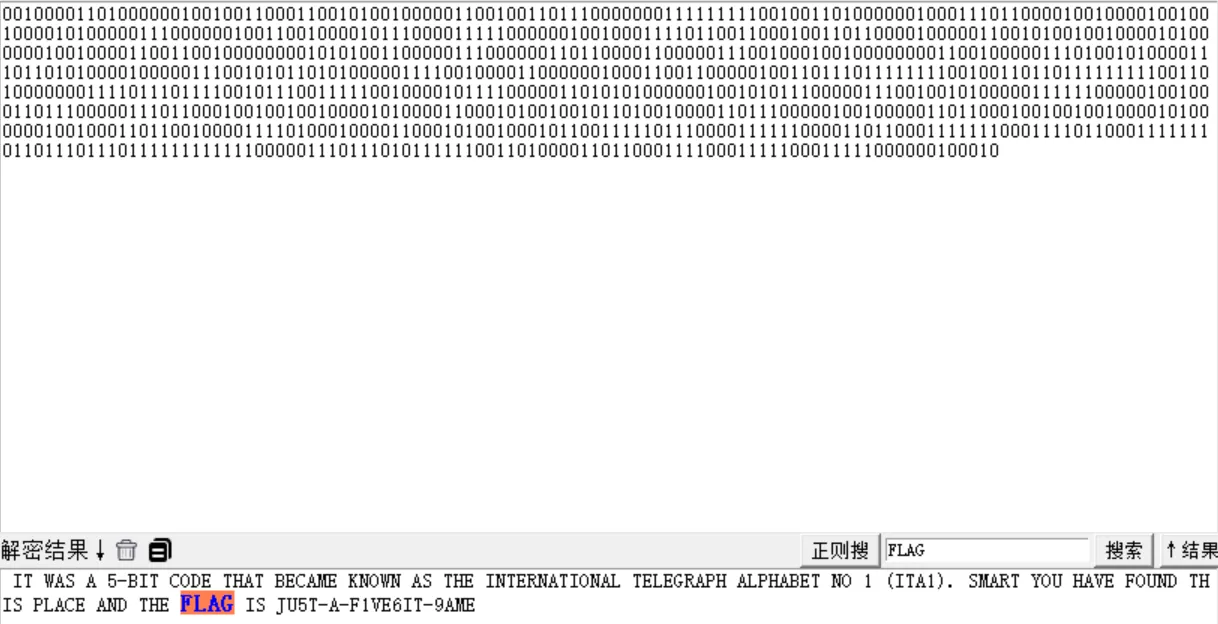
# 001000011010000001001001100011001010010000011001001101110000000111111111001001101000000100011101100001001000010010010000101000001110000001001100100001011100001111100000010010001111011001100010011011000010000011001010010010000101000000100100001100110010000000010101001100000111000000110110000110000011100100010010000000011001000001110100101000011101101010000100000111001010110101000001111001000011000000100011001100000100110111011111111001001101101111111110011010000000111101110111100101110011111001000010111100000110101010000001001010111000001110010010100000111111000001001000110111000001110110001001001001000010100001100010100100101101001000011011100000100100000110110001001001001000010100000010010001101100100001111010001000011000101001000101100111110111000011111100001101100011111110001111011000111111101101110111011111111111100000111011101011111100110100001101100011110001111100011111000000100010根据题目意思,五位以及five.png可以联想博多码,所以用随波逐流直接梭
在CTF中,博多码(Baudot/ITA2)的核心特征是:数据为5的倍数位(二进制)或0-31的数字序列;最关键的是包含两个特殊的控制字符:十进制27(0x1B, 二进制11011)是FIGS(数字换档),31(0x1F, 二进制11111)是LTRS(字母换档),它们会交替出现。解码必须根据换档符在字母和数字两种字符集间切换。
DASCTF{JU5T-A-F1VE6IT-9AME}
题目名称 Infinite_transformation
磁盘里蕴含着什么东西呢,也许有一只猫
根据压缩包提示可以爆破出密码为121144
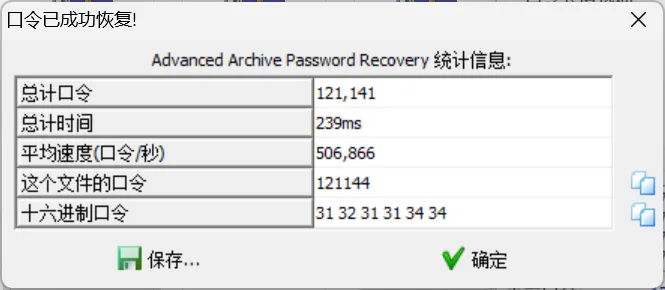
解压后得到一个vmdk虚拟磁盘文件,通过挂载和数据恢复拿到
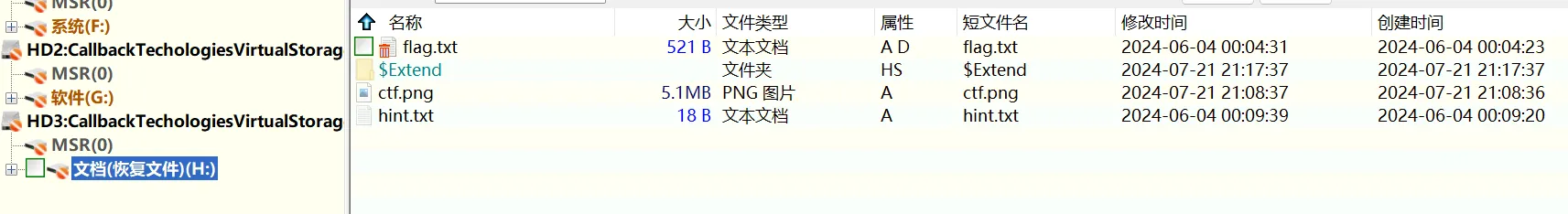
得到两个txt和一个图片
flag.txt:
64302039943980618121484184873128503074609076299244422107146064367058121738007282650851520841656649070683123403821937513267391370346165645908933956953599129037238861474390287394253991334205788122863003605507035424785292830536282067025856204240859500900770386319047433635878298987553848841486636769829855797015618861382395619672208366605793866695702843978585628878996390708495917362310741277717465790690657480858197797078816624813513712771929056001109014477328987890335180242509040895793315048815591172058129474723554263040
hint.txt:
数字映射函数
ctf.png:
对图片分析可以看见色道存在问题
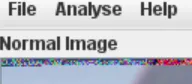
使用stegsolve对RGB通道的第七位查看,发现隐写了一张PNG图片
隐写的图片:
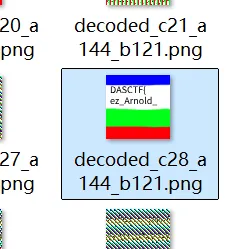
根据提示和压缩包密码可以猜测为猫脸变换
这里可以使用Github项目进行直接爆破,参数a、b根据压缩包密码可以猜测出
这里就得到了第一段flag:DASCTF{ez_Arnold_
对于hint给的提示也是一脸懵逼,对这一长串十进制数字进行各种解码也没啥思路,后面发现Tupper自指公式
可以在这个在线工具进行绘制:[https://tuppers-formula.ovh/](https://tuppers-formula.ovh/)
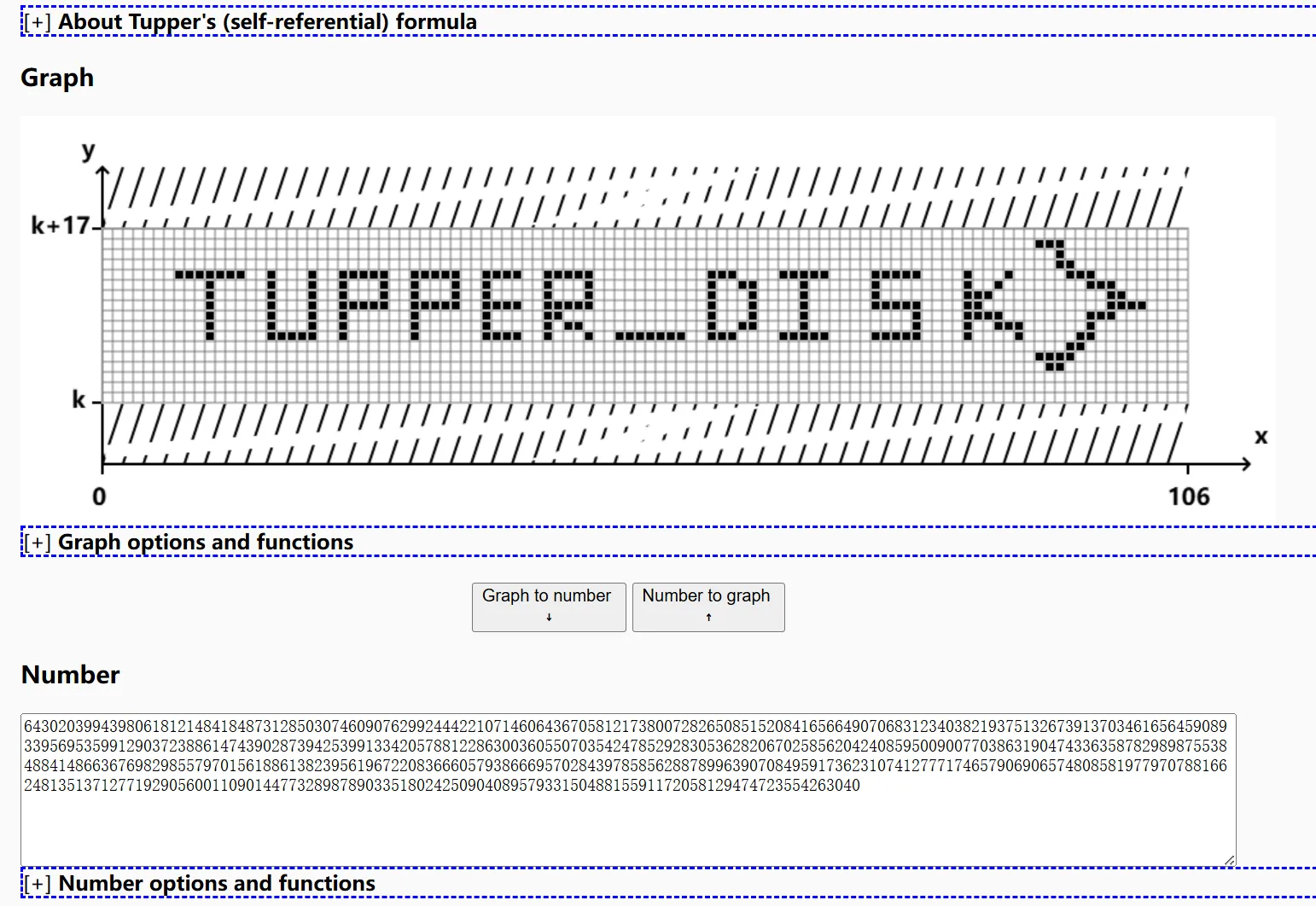
拿到后半段:TUPPER_DISK}
结合一下可以获得完整flag:DASCTF{ez_Arnold_TUPPER_DISK}









评论已关闭